Integrated Security Solutions
Closed-circuit television (CCTV) surveillance systems have made tremendous technological progress in the last decade, not only in individual capabilities, but also in the ability to interface with other security technology.
There are three primary ways to use CCTV systems, industry experts say: as a deterrent, for forensic purposes and as an interdictive device.
As recording and storing technologies and software such as video analytics have became more efficient, CCTV surveillance systems have evolved into a forensic tool — that is, collecting evidence after an event has occurred. But as CCTV surveillance systems become more easily integrated with monitoring devices, alarm systems and access control devices, a third use of CCTV is gaining momentum: Helping security personnel to identify and interrupt security breaches as they’re occurring, or even before they take place.


Intelligent video algorithms, such as sophisticated motion detection, can identify unusual walking patterns and alert a guard to watch a particular video screen. Object-recognition algorithms can identify someone who might simply be loitering, or even a briefcase or other suspicious object that is left somewhere it shouldn’t be. Again, the system can alert a monitoring guard so that appropriate action can be taken.
The most advanced intelligent video algorithm is facial recognition. However, most experts agree that use of this technology as an efficient tool in the private sector is still several years down the road.
Our Technical experts plan, design and implement the entire range of new technology to secure your infrastructure/premises. Security has been our top priority since decades.
We add an extra step to your security system by adding door readers, electric locks, a controller, and management software. Its purpose is to limit access to people who are authorized to enter an organization. It uses door readers that detect the unique identification numbers provided by credentials. A credential can be an RFID card or keyFob, a person’s smartphone, or their biometric (ie. face or fingerprint) credential.
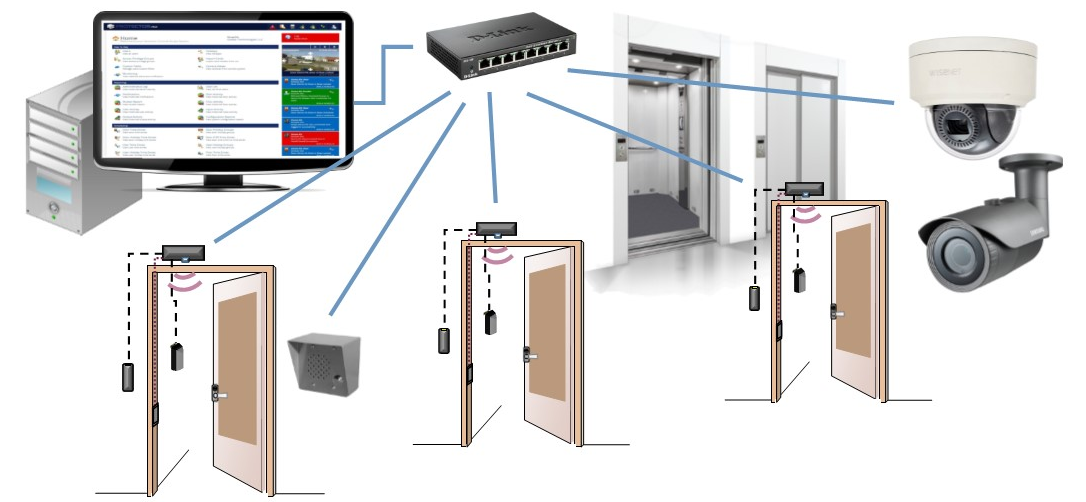
CTS’s Portfolio for Access Control System are as follows
We are a technology driven company
Our technical team and technicians are perfectionlists who love what they do and love where they work

Head Office
755/1975, Khandayat SahiMangalabag, Cuttack-753001, Odisha

Give Us A Call
(+91) 8978557277(+91) 9861116510

Help Desk
info@concentric-techs.com